26/05/2013
20/05/2013
Inventors of Computer Hardware
1:Key board— Herman Hollerith, first keypunch
devices in 1930’s
-
2:Transistor— John Bardeen, Walter Brattain & Wiliam
Shockley ( 1947-48)
-
3:RAM— An Wang and Jay Forrester (1951)
-
4:Trackball— Tom Cranston and Fred Longstaff (1952)
-
5:Hard Disk— IBM , The IBM Model 350 Disk File (1956 )
-
6:Integrated Circuit— Jack Kilby & Robert Noyce
( 1958)
-
7:Computer Mouse — Douglas Engelbart (1964)
-
8:Laser printer— Gary Starkweather at XEROX in1969.
-
9:Floppy Disk— Alan Shugart &IBM( 1970)
-
10:Microprocessor— Faggin, Hoff & Mazor – Intel 4004
(1971)
The first computer mouse
The first computer mouse was invented in 1963 by Douglas Engelbart at the Stanford Research Institute. (He is also one of the inventors of hypertext.) The first mouse used two wheels positioned at a 90-degree angle to each other to keep track of the movement (see picture below). The ball mouse wasn’t invented until 1972, and the optical mouse was invented circa 1980 although it didn’t come to popular use until much later.
Douglas Engelbart never received any royalties for his invention and his patent had run out by the time the mouse became commonplace in the era of home PCs.

Above: The first mouse. To the right you can see the wheels it used for movement and positioning.
devices in 1930’s
-
2:Transistor— John Bardeen, Walter Brattain & Wiliam
Shockley ( 1947-48)
-
3:RAM— An Wang and Jay Forrester (1951)
-
4:Trackball— Tom Cranston and Fred Longstaff (1952)
-
5:Hard Disk— IBM , The IBM Model 350 Disk File (1956 )
-
6:Integrated Circuit— Jack Kilby & Robert Noyce
( 1958)
-
7:Computer Mouse — Douglas Engelbart (1964)
-
8:Laser printer— Gary Starkweather at XEROX in1969.
-
9:Floppy Disk— Alan Shugart &IBM( 1970)
-
10:Microprocessor— Faggin, Hoff & Mazor – Intel 4004
(1971)
The first computer mouse
The first computer mouse was invented in 1963 by Douglas Engelbart at the Stanford Research Institute. (He is also one of the inventors of hypertext.) The first mouse used two wheels positioned at a 90-degree angle to each other to keep track of the movement (see picture below). The ball mouse wasn’t invented until 1972, and the optical mouse was invented circa 1980 although it didn’t come to popular use until much later.
Douglas Engelbart never received any royalties for his invention and his patent had run out by the time the mouse became commonplace in the era of home PCs.
Above: The first mouse. To the right you can see the wheels it used for movement and positioning.
The first trackball
The trackball was actually invented 11 years BEFORE the mouse, in 1952. It was invented by Tom Cranston and Fred Longstaff as part of a computerized battlefield information system called DATAR, initiated by the Canadian Navy. It used a standard five-pin bowling ball as its trackball, which is smaller than the more common 10-pin bowling ball.

Above: The first trackball, bowling ball and all.
The trackball was actually invented 11 years BEFORE the mouse, in 1952. It was invented by Tom Cranston and Fred Longstaff as part of a computerized battlefield information system called DATAR, initiated by the Canadian Navy. It used a standard five-pin bowling ball as its trackball, which is smaller than the more common 10-pin bowling ball.
Above: The first trackball, bowling ball and all.
The first portable computer
Well, perhaps that should be “movable” computer… The IBM 5100 Portable Computer was introduced in 1975, weighed 25 kg (55 lb), was the size of a small suitcase and needed external power to operate. It held everything in the same unit, packing in a processor, ROM (several hundreds of KB) and RAM (16-64 KB), a five-inch CRT display, keyboard and a tape drive, which was an amazing feat at the time. It also came with built-in BASIC and/or APL. The different models of the IBM 5100 sold for $8,975 – $19,975.

Above: The IBM 5100 Portable Computer.
Well, perhaps that should be “movable” computer… The IBM 5100 Portable Computer was introduced in 1975, weighed 25 kg (55 lb), was the size of a small suitcase and needed external power to operate. It held everything in the same unit, packing in a processor, ROM (several hundreds of KB) and RAM (16-64 KB), a five-inch CRT display, keyboard and a tape drive, which was an amazing feat at the time. It also came with built-in BASIC and/or APL. The different models of the IBM 5100 sold for $8,975 – $19,975.
Above: The IBM 5100 Portable Computer.
The first laptop computer
The first laptop computer (or notebook) was the Grid Compass 1100 (called the GRiD) and was designed in 1979 by a British industrial designer, Bill Moggridge. The computer didn’t start selling until 1982, then featuring a 320×200 screen, an Intel 8086 processor, 340 KB of magnetic bubble memory (a now obsolete, non-volatile memory type) and a 1200 bps modem. It weighed 5 kg (11 lb) and cost $8-10,000. The GRiD was mainly used by NASA and the US military.

Above left: Closeup of the Grid Compass 1100. Above right: NASA astronaut posing with the GRiD in space (that’s Spock on the screen.)
The first laptop computer (or notebook) was the Grid Compass 1100 (called the GRiD) and was designed in 1979 by a British industrial designer, Bill Moggridge. The computer didn’t start selling until 1982, then featuring a 320×200 screen, an Intel 8086 processor, 340 KB of magnetic bubble memory (a now obsolete, non-volatile memory type) and a 1200 bps modem. It weighed 5 kg (11 lb) and cost $8-10,000. The GRiD was mainly used by NASA and the US military.
Above left: Closeup of the Grid Compass 1100. Above right: NASA astronaut posing with the GRiD in space (that’s Spock on the screen.)
The first IBM PC
The IBM Personal Computer was introduced in 1981 as the IBM 5150. The platform became so pervasive in the 80s that although the term “personal computer” had been in use since the early 70s, a PC became synonymous with an IBM PC-compatible computer.
During its development, the IBM 5150 had been internally referred to as “Project Chess” and was created by a team of 12 people headed by Don Estridge and Larry Potter. To speed up development and cut costs, IBM had decided to use off-the-shelf parts, something that they normally wouldn’t do.
The first IBM PC had an Intel 8088 processor, 64 KB of RAM (extendible to 256 KB), a floppy disk drive (which could be used to boot the computer with a rebranded version of MS-DOS (PC-DOS)) and a CGA or monochrome video card. The machine also had a version of Microsoft BASIC in ROM. On the first IBM PC the optional 10 MB hard disk drive could only be installed if the original power supply was replaced (the original one was too weak).

Above: The first IBM Personal Computer, the IBM 5150.
The IBM Personal Computer was introduced in 1981 as the IBM 5150. The platform became so pervasive in the 80s that although the term “personal computer” had been in use since the early 70s, a PC became synonymous with an IBM PC-compatible computer.
During its development, the IBM 5150 had been internally referred to as “Project Chess” and was created by a team of 12 people headed by Don Estridge and Larry Potter. To speed up development and cut costs, IBM had decided to use off-the-shelf parts, something that they normally wouldn’t do.
The first IBM PC had an Intel 8088 processor, 64 KB of RAM (extendible to 256 KB), a floppy disk drive (which could be used to boot the computer with a rebranded version of MS-DOS (PC-DOS)) and a CGA or monochrome video card. The machine also had a version of Microsoft BASIC in ROM. On the first IBM PC the optional 10 MB hard disk drive could only be installed if the original power supply was replaced (the original one was too weak).
Above: The first IBM Personal Computer, the IBM 5150.
The first Apple computer
The first Apple personal computers (Apple I) were designed and hand-built by Steve Wozniak. The Apple I went on sale in 1976 for the price of $666.66. Only about 200 units were produced. The Apple I was basically just a motherboard with a processor, a total of 8KB of RAM, a display interface and some additional functionality. To have a working computer, the buyer would have to add a power supply, a keyboard and a display (and a case to keep mount it all in).

Above left: An Apple I computer. Above right: This was the Apple I, essentially a motherboard.
The first Apple personal computers (Apple I) were designed and hand-built by Steve Wozniak. The Apple I went on sale in 1976 for the price of $666.66. Only about 200 units were produced. The Apple I was basically just a motherboard with a processor, a total of 8KB of RAM, a display interface and some additional functionality. To have a working computer, the buyer would have to add a power supply, a keyboard and a display (and a case to keep mount it all in).
Above left: An Apple I computer. Above right: This was the Apple I, essentially a motherboard.
The first RAM
Arguably the first (writable) random access memory was Magnetic Core Memory (also called Ferrite-Core Memory) and was invented in 1951 as a result of work done by An Wang at Harvard University’s Computation Lab and Jay Forrester at MIT.
Core memory was a family of related technologies that used the magnetic properties of materials to give them a similar functionality to transistors. They stored their information using the polarity of tiny, magnetic ceramic rings with wires threaded through them. Unlike today’s RAM, core memory could keep its information even after the power was turned off.
Core memory was common until it was replaced by integrated silicon RAM chips in the 1970s. The “core” in core memory is why a memory dump is called a “core dump” even today.

Above left: Closeup of core memory. Above right: The core memory plane in the picture is 16×16 cm (6.3×6.3 inches), holding 128×128 bits (2048 byte).
Arguably the first (writable) random access memory was Magnetic Core Memory (also called Ferrite-Core Memory) and was invented in 1951 as a result of work done by An Wang at Harvard University’s Computation Lab and Jay Forrester at MIT.
Core memory was a family of related technologies that used the magnetic properties of materials to give them a similar functionality to transistors. They stored their information using the polarity of tiny, magnetic ceramic rings with wires threaded through them. Unlike today’s RAM, core memory could keep its information even after the power was turned off.
Core memory was common until it was replaced by integrated silicon RAM chips in the 1970s. The “core” in core memory is why a memory dump is called a “core dump” even today.
Above left: Closeup of core memory. Above right: The core memory plane in the picture is 16×16 cm (6.3×6.3 inches), holding 128×128 bits (2048 byte).
The first hard disk drive
The IBM Model 350 Disk File was the first hard disk drive and was part of the IBM 305 RAMAC computer that IBM started delivering in 1956 (mainly intended for business accounting). It had 50 24-inch discs that together could store about 4.4 MB of data. The Model 350 spun at 1200 rpm, had a data transfer rate of 8,800 characters per second and an access time of approximately one second.

Above: The first hard disk drive, IBM Model 350.
The IBM Model 350 Disk File was the first hard disk drive and was part of the IBM 305 RAMAC computer that IBM started delivering in 1956 (mainly intended for business accounting). It had 50 24-inch discs that together could store about 4.4 MB of data. The Model 350 spun at 1200 rpm, had a data transfer rate of 8,800 characters per second and an access time of approximately one second.
Above: The first hard disk drive, IBM Model 350.
The first laser printer
The laser printer was invented by Gary Starkweather at XEROX in 1969. His initial prototype was a modified laser copier where he had disabled the imaging system and introduced a spinning drum with eight mirrored sides. The first commercial implementation of a laser printer didn’t happen until IBM released the IBM model 3800 in 1976. It could pretty much fill up a room on its own.

Above: The IBM 3800, the first commercial laser printer.
The laser printer was invented by Gary Starkweather at XEROX in 1969. His initial prototype was a modified laser copier where he had disabled the imaging system and introduced a spinning drum with eight mirrored sides. The first commercial implementation of a laser printer didn’t happen until IBM released the IBM model 3800 in 1976. It could pretty much fill up a room on its own.
Above: The IBM 3800, the first commercial laser printer.
The first web server
And since the Web is such an integral part of today’s computer experience, we couldn’t help but include another first: The first web server was a NeXT workstation that Tim Berners-Lee used when he invented the World Wide Web at CERN. The first web page was put online on August 6, 1991.
The computer had a note on it that said, “This machine is a server. DO NOT POWER IT DOWN!!” Understandable, considering that if you had shut it down in the early days you would have shut down the entire WWW.

Above: The web server that powered the first web pages on the WWW. Note the sticker with the warning to not turn it off.
It’s amazing how much has happened in the PC industry in just a few decades. Just imagine what things will be like 30-40 years from now…???
And since the Web is such an integral part of today’s computer experience, we couldn’t help but include another first: The first web server was a NeXT workstation that Tim Berners-Lee used when he invented the World Wide Web at CERN. The first web page was put online on August 6, 1991.
The computer had a note on it that said, “This machine is a server. DO NOT POWER IT DOWN!!” Understandable, considering that if you had shut it down in the early days you would have shut down the entire WWW.
Above: The web server that powered the first web pages on the WWW. Note the sticker with the warning to not turn it off.
It’s amazing how much has happened in the PC industry in just a few decades. Just imagine what things will be like 30-40 years from now…???
16/05/2013
DIFFERENCE BETWEEN CORE I3, CORE I5, CORE I7...??
Core i3:
* Entry level processor.
* 2-4 Cores
* 4 Threads
* Hyper-Threading (efficient use of processor resources)
* 3-4 MB Catche
* 32 nm Silicon (less heat and energy)
Core i5:
* Mid range processor.
* 2-4 Cores
* 4 Threads
* Turbo Mode (turn off core if not used)
* Hyper-Threading (efficient use of processor resources)
* 3-8 MB Catche
* 32-45 nm Silicon (less heat and energy)
* Mid range processor.
* 2-4 Cores
* 4 Threads
* Turbo Mode (turn off core if not used)
* Hyper-Threading (efficient use of processor resources)
* 3-8 MB Catche
* 32-45 nm Silicon (less heat and energy)
Core i7:
* High end processor.
* 4 Cores
* 8 Threads
* Turbo Mode (turn off core if not used)
* Hyper-Threading (efficient use of processor resources)
* 4-8 MB Catche
* 32-45 nm Silicon (less heat and energy)
* High end processor.
* 4 Cores
* 8 Threads
* Turbo Mode (turn off core if not used)
* Hyper-Threading (efficient use of processor resources)
* 4-8 MB Catche
* 32-45 nm Silicon (less heat and energy)
08/05/2013
Ways to protect your Facebook account
Ways to protect your Facebook account
Protecting Facebook account is very much important nowadays. A lot of people are facing this common issue of protecting Facebook account. People are simply creating their Facebook account and are posting all personal information in it in no time. But they never try to protect it. Simple things will make your account to be hacked by any common friend of yours. Today i will tell you how to protect your Facebook account from being hacked.
And its not a must that only a professional hacker can hack a Facebook account, It can be anyone who have a minimum common sense of using the proper information at proper place. Since Facebook is no where connected or bothered about the security issues of your email id, which are Gmail/ yahoo. we cant guarantee that our Facebook account is in safe hands. If once you have lost access to your email address, the hacker have obviously gained access to your Facebook account. Let us understand few basic steps of protecting Facebook account.
Don’t Display your Facebook Account Id :This is a very common mistake which everyone does. We just display our Facebook login ID details in our info page on Facebook. Which is a direct hint to the hacker saying which ID you are using to login the Facebook account. If you are not getting my point.. Just watch out the screenshot below.
Protecting Your Respective Facebook Account Id : This means, for example if you are using your Gmail account to login your Facebook account, You have to make sure that your Gmail account is properly secured. This is the most important concept which people usually forget to note. Secure your Gmail account from any possible way to hack your account. And if you are using Yahoo mail or Any other mail service, make sure they are properly verified. Which means you have to verify it with other alternate email or atleast connecting with your phone.
Keep Changing Your Passwords :You must change the passwords frequently to secure your account. You can use special characters in your passwords like !@#$ and %^&& to make it very tough for the hacker to crack it and guess it. Also remember that, you should never ever share your password with anyone. A strong password is always a plus point in protecting Facebook accounts.
Connect Your Mobile Phone :You can connect your mobile phone to your Facebook account, so that when ever your account has been compromised. You can get a security code to your phone to get back to your Facebook account. You can connect your mobile phone in the Mobile tab in Account Setting Options. Take a look at the screenshot below.
You can also add more than one phone to your account to protect your account. Just go to Account tab in Facebook which is beside Home and Profile and again in Account tab, select Account Settings which will navigate to above options page. Here you can edit any information which you want to.
Enable Secure Browsing :The normal Facebook account is set to HTTP browsing which is less secured when compared to HTTPS. When you enable the secure browsing, you can find a lot of changes in your Facebook browsing. Your account will be more secured from virus and spam posts. Also you can get notifications on the change of location if anyone is trying to hack your account.You can find this option in Account -> Account Settings -> Security.
Login Notifications :You can make Facebook to send you messages to your Mobile and Email if you are tying to login from a different computer. This way you can be more alert in changing your passwords often. I use this service with my Facebook account which is very useful for us to get update on what is happening with our Facebook account. You can find this option in Account -> Account Settings -> Security.
Active Sessions : This will allow you to see the last and the current session which have been active with your account. For example if you have find any unfamiliar locations, you can click the end activity to close the session. With this you are blocking the person to access your account from that location. You can find this option on Account -> Account Settings -> Security which is the last option.
Remembering Passwords :When even you are browsing in any Internet cafe or at friend home, Make sure that you wont allow the browser to save your passwords. If it offers to save the passwords, Just ignore it and move on.
Get your Account back : If at all your Facebook account is being hacked. Just make sure that you are still able to login your respective email id, which is Gmail, yahoo or any other and if not possible to login there, just come to Facebook home page and click on Forgot Password and restore the link to any other alternate email id or to your phone to get you Facebook account back If even that is being changed. Make sure you have 3 good friends in your account who can refer you to get your account back. Just click on No longer have access to these? Link in forgot password page and enter a new alternate email id and then wait for a day to get a confirmation message to change your password. For that you have set your security question too. Which cant be changed that easily.
Look For Key loggers & Phishing Sites : Always suspect a chance of getting affected by a key logger in any Internet cafe or at friend home. Generally a key logger will store all the data which you enter in a system, storing all your passwords, chats and any other alternative things which you have done with your keyboards. And remember Facebook will never ask you to login from anonymous mails and places to verify yourself. If any Facebook App is trying to ask your Facebook Account ID and Password, Just ignore it. Most of them are phishing pages where your Login details will be sent to a hacker within no time. Never login facebook account from other 3rd party links. Directly login from www.facebook.com. So don’t ever login to your Facebook in any where unless you trust that place well and good.
These are the 10 few simple ways of protecting Facebook account from being hacked. Just follow them and apply carefully to get rid of hackers and intruders. Protecting Facebook account is not that difficult now.
07/05/2013
Make your PC welcome You in computer voice
Make ur PC welcome u in computer voice......(Trick)
1. Click on Start. Navigate to All Programs, Accessories and Notepad.
2. Copy and paste the codes given below.
Dim speaks, speech
speaks="Welcome to your PC, Username"
Set speech=CreateObject("sapi.spvoice")
speech.Speak speaks
3. Replace Username with your own name.
4. Click on File Menu, Save As, select All Types in Save as Type option, and save the file as Welcome.vbs or “*.vbs”.
5. Copy the saved file.
6. Navigate to C:\Documents and Settings\All Users\Start Menu\Programs\Startup (in Windows XP)
Or
C:\Users \User-Name\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup (in Windows Vista or in Windows 7 or in Windows
8 ) if C: is your System drive (Operation system Drive).
7. Paste the file.
Now when the next time you start your computer, Windows will welcome you in its own computer voice.
Note: For best results, it is recommended to change sound scheme to No Sounds.
You can change the sound scheme to No Sounds by following the steps given below:-
Go to Control Panel.
Then click on Switch to Classic View.
Then Click on Sounds and Audio Devices.
Then Click on the Sounds Tab.
Select No Sounds from the Sound Scheme option.
If you wish to save your Previous Sound Scheme, you can save it by clicking Yes in the popup menu.
Click on OK.
Have Fun ……………
LET’S CELEBRATE… I made it to 1,000 hits today! THANK YOU!
LET’S
CELEBRATE… I made it to 1,000 hits today! THANK YOU!
Hello
everyone, just a quick word from me… I made it to 1,000 hits today. Thank you very much to everyone who has taken
the time to read my blog and visit my pages.
I decided to
write a blog a few months ago, so that I could share my passion with
others. At first I wasn’t sure I was
going to be any good at it and wondered what my aim was, now i have fallen in love with blogging.
I’ve really enjoyed writing this blog and I’ve to admit that I’m a bit addicted to refreshing my blog to see if anyone has liked, commented or even followed. It gives me a major thrill to see visitors from all over the world checking out my blog. I don’t have a huge army of followers yet but that doesn’t disappoint me. I enjoy blogging and I feel happy seeing people read each of them. It’s like getting connected with people from all over the world, without actually knowing them.
I set myself
a few goals last month and today I reached my first one! Knowing that people are reading articles is really great. So thanks again and please do keep reading…
Wow, it feels great to see my blog cross over the magic mark of 1000 hits! Thank you so much, my dear readers!!!
Nimma G!R!SH
AMAZING FACTS ABOUT INTERNET & some abbreviations
AMAZING FACTS ABOUT INTERNET DID YOU KNOW ABOUT IT
Happy birthday to the World Wide Web; the project turned 20 this past April..
We use it every day; you’re using it right now and so are about 2.2 billion other people. But how much do you really know about it?
On April 30, 1993, CERN (the European Organization for Nuclear Research) gave birth to the World Wide Web.
Check out these facts about the spectacular internet, and remember..!!
users on the Internet is 2.2
billion! In 2006, this number
was only 600 million. So in a
decade, the internet users have
grown by almost 370%
2. Facebook.com ingests over
500 Terabytes of Data every
day. This includes 2.7 million
Likes and 300 million photo
uploads, daily! (Source – CNet)
3. Up to 40% of all accounts and
8% of all messages on social
media sites are created by
Spammers. (Source-
Bloomberg)
4. Every month, Google, the
world’s leading Search engine
handles 100 Billion Searches!
That equates to almost 40,000
every second. Yes, 40,000!
5. The first Webcam was
created at the University of
Cambridge, UK. Can you guess
what was it used for? Well,
they used it to monitor a
coffee pot!
6. The world’s first website
and web server was launched
on August 6th, 1991. It was
published by Tim Berbers Lee,
and the website URL was
Info.cern.ch
7. The world’s most expensive
domain name ever sold is
Insure.com at $16 million.
Sex.com comes next, which
was sold for $14 million.
8. Internet usage is highest in
Iceland, where 97.8% of its
population uses the internet.
In USA, it was 78.3%, China
38.4% and North Korea lowest
at 0%.
9. Philip M. Parker designed an
algorithm that makes Books
from info found on the web.
The “world’s most prolific
author” has created over
200,000 books!
10. How much does the
internet weigh? The weight of
all information on the internet
is 0.2 millionths of an Ounce.
That is similar to the weight of
the smallest possible grain of sand.
There are 7 people in the world who hold the “key to the internet.” If in the event of a major catastrophe the internet is shut down these key holders will together be able to reboot an integral part of the system.
Nowadays we have Mozilla Firefox & Internet Explorer but the very first widely popular web browser was Mosaic which was available from 1993 and discontinued in 1997.
The internet accrued 50 million users in just 5 years. It took TV 13 years to do that.
A surfing session lasts on average just under an hour for most people – 51 minutes to be exact.
75% of Swedish people use the internet making them the country with the largest percentage of internet users.
With satellite based internet now available there is no country in the world that cannot access the internet although Governments in certain countries still continue to severely restrict its use. In North Korea only Government officials and named officers have access to the net and China is famous for restricting its public’s access to certain sites.
People who use social networking sites such as Facebook and Twitter will use 10% of their entire life time on these sites.
As a continent Asia has the largest number of internet users at 42% and this looks set for massive growth as infiltration of the net is still at 20%, meaning 80% is still not using it.
19% of married couples meet online, making it the most successful method for meeting the “one.” Following an online introduction the most successful methods for meeting a future wife or husband continues to be through work or friends, with each of these methods getting 17% of married couples together.
Each day, about 20 million people “tweet”. Internet experts speculate that over half of all tweets are based on controversial subjects.
The first internet banner ad was launched in 1994 and it ended up being a huge hit because people just couldn’t resist clicking. It looks like an older ad, but the same strategies are used by advertisers today.
The United States is actually in third place currently for the world’s most internet users. Asia easily comes in first with about 36% while Europe is in second with 29% and the States get a disappointing bronze medal with 21%. On the other hand, Americans are #1 for the most people who use the internet and watch TV simultaneously and also easily get the gold for the most bloggers.
About 1/6 of Earth’s total population enjoys surfing the internet at least once per month. Many of the people who do not surf the internet, however, have noted that they would like to enjoy internet pictures and videos if they had the opportunity.
About 15 hours of video are uploaded to Youtube from around the globe each minute. After reading about this, I now know why the site typically has a limit of 10 minutes per video.
* CD - Compact Disk.
* DVD - Digital Video Disk.
* AM - Ante Meredian.
* PM - Post Meredian.
* AD - AnnoDomini.
* BC - Before Christ .
* FM - Frequency Modulation.
* GPRS - General Packet Radio
Service.
* USB - Universal Serial Bus.
* www - World Wide Web.
* Http - Hypertext Transfer
Protocol.
* HTML - Hypertext Mark
Language.
* LAN - Local Area Network.
* SIM - Subsciber Identity
Module .
* GSM - Global System for Mobile.
* WLAN - Wireless Local
Network.
* SQL - Structured Query
Language.
* XSS/CSS - Cross Site Scripting
* LFI - Link Fragmentation and
Interleaving .
90% of Your Friends Dont know
this plz Share .
06/05/2013
How to Get New News Feed on Facebook?
How to Get New News Feed on Facebook?
Facebook the best social networking site in world.Always trying to get more helpful features to users.Recently Facebook launched Graph search now they have concentrated on news feed.its very helpful.previously you find all stories in one place but now they have filtered them with different options.just look how the new design of news feed in below Gif.

News Feed new design Features:As i told above new design of news feed has added more features like a clean look with large photos, and be sorted by following categories like:

All Friends: here you can find every thing your friends are sharing
Photos: you can get photos of your friends and from pages you like onFacebook
Music: its all about the Music you listen and your friends.
Following: here you get news from the people you follow.The new design of News feed will give posts like places and third-party apps more prominence and bigger images. Videos,pictures and other shared articles will also get a new look. Now,a thumbnail appear on the left side who tagged in a video or those who shared video.
How to get New News Feed:There is a waiting list for who want to get New News'feed on their facebook.
Just login to your facebook account
Now click here to get News' feed
Now scroll down to bottom of page you can something just like below scrren capture

Now click Join Waiting List.thats it now you're on the list.
When you get New News Feed on your Facebook You can see a message at the top of your feed.
.jpg)
Just click on Give It a Try and now you will enable this feature.
Visit this link https://www.facebook.com/about/newsfeed to know more....
05/05/2013
How To Access Facebook Without Internet Connection ?
How to Access Facebook without Internet Connection & without any Data Charges
Now a days everyone start using FB but much of them don't know FB can access without internet also ..!!
How it Works:
Just dial *325# or *fbk# from your mobile and wait for the confirmation message on the screen. Give your username and password to access Facebook without any Data Charges
USSD is Rs. 1 / day for unlimited usage!
Note:-This service is currently available on Airtel, Aircel and Tata Docomo (India)
1. Now, you can update your Face book status on free of cost.
2. Now, you can View, comment on photo, like any post, post on friend wall, confirm friend requests, view notifications, find new friends, add friends at cost Re -1 / day per use.
You can use No.1 social network Facebook on Airtel mobile without GPRS connectivity or Wifi Connectivity.
It means without Browser or Internet you can do facebooking using Bharti Airtel.
It means without Browser or Internet you can do facebooking using Bharti Airtel.
Dial *325*22# and you will be unsubscribed form the Airtel service.
Now Idea n/w is also providing the same service & even u can get d B'day remainders also it ll helps you when u r using basic handsets..
04/05/2013
Difference Between Virus,Worms,Trojan and Spyware
Difference Between Virus,Worms,Trojan and Spyware
We all have heard the terms Virus,Worms,trojans and spyware but only a few of us know the difference between them.We genreally consider everything that is detected by an antivirus as virus but this is not the case.The antivirus not only provides protection against viruses but it also protects us from trojans,worms and spywares.All these can be harmful to your computer hardware and software.Today I will differentiate all these terms from each other .
Ok lets start from the introduction of viruses
Virus:-A virus is a self replicating program that attaches itself to an executable file.When the file is executed the virus automatically gets executed and enters into system memory .Once it enters into system memory it either searches for other files that can be infected or stays in the background and infect the files that are uses the virus infected program.
Worms:Worms are very similar to viruses but differ in way that they donot bind themselves to executable files instead to replicate themselves they uses the network.If you find excessive use of your network bandwidth then you may be infected by a worm.So,a worm donot require a user to execute any file for its execution it can work without user intervention.
Trojan Horse:-A trojan horse is harmful program which may seem harmless to the user before its installation but instead it is programmed or reverse engineered to facilitate unauthorised remote access to the computer.Trojan’s donot replicate themselves.
Spyware:-A spyware is a program that secretly monitor and collects pieces of information.They usually run in stealth mode and cannot be detected easily.Keyloggers is a great example of spyware software.These are not limited to just spying but can also send data to remote computers .
We all have heard the terms Virus,Worms,trojans and spyware but only a few of us know the difference between them.We genreally consider everything that is detected by an antivirus as virus but this is not the case.The antivirus not only provides protection against viruses but it also protects us from trojans,worms and spywares.All these can be harmful to your computer hardware and software.Today I will differentiate all these terms from each other .
Ok lets start from the introduction of viruses
Virus:-A virus is a self replicating program that attaches itself to an executable file.When the file is executed the virus automatically gets executed and enters into system memory .Once it enters into system memory it either searches for other files that can be infected or stays in the background and infect the files that are uses the virus infected program.
Worms:Worms are very similar to viruses but differ in way that they donot bind themselves to executable files instead to replicate themselves they uses the network.If you find excessive use of your network bandwidth then you may be infected by a worm.So,a worm donot require a user to execute any file for its execution it can work without user intervention.
Trojan Horse:-A trojan horse is harmful program which may seem harmless to the user before its installation but instead it is programmed or reverse engineered to facilitate unauthorised remote access to the computer.Trojan’s donot replicate themselves.
Spyware:-A spyware is a program that secretly monitor and collects pieces of information.They usually run in stealth mode and cannot be detected easily.Keyloggers is a great example of spyware software.These are not limited to just spying but can also send data to remote computers .
Technical News..
Some Technical news..
India's first 1Gbps Internet connection...
Google, launched its 1000mbps (1gbps) at kansas city (US), a leading techn incubator in US, as part of the Google Fiber Network. and Now, it is India's turn to get this speed.
Kerala, India's first telecom company incubator now has a new 1Gbps connectivity, Startup village of Kochi has become the second place in the world, after Kansas city of US.
Start up Village aims to build the elements of a world class tech ecosystem to realize the dream of a Silicon Coast in INDIA.
you can download a two-hour HD movie in 30 seconds or view 1080p video in YouTube at this lightning speed ....
#addy#

Want to know the Manufacturing Date of Your computer ?
Open Cmd and Type
-debug
Enter then type
- DF000:FFF5
Hit Enter...
DID YOU KNOW??
Facebook paid a whooping $8.5 Million to buy "Fb.com" domain!! So next time instead of typing "facebook.com" you can just type in "Fb.com" to save time!!
Languages Used....
1. Google – Java (Web), – C++ (indexing)
2. Facebook – PHP
3. YouTube- Flash, Python, Java
4. Yahoo– PHP and Java
5. Microsoft Live.com– .NET
6. Baidu – Unknown
7. Wikipedia – PHP
8. Blogger – Java
9. MSN – .NET
10.Twitter – Ruby on Rails, Scala, Java
|Find Serial-Key for any software
1. Those who use trial versions of softs..
2. Go to GOOGLE.com
3. Type '94fbr' Then space and then name of software u need..
4. Google will show u links with ur desired serial key or patch files..
SOME INTERESTING FACTS ABOUT GOOGLE:
1. The name GOOGLE was an accident. A spelling mistake made by the original founders who thought they were going for GOOGOL. Googol is a mathematical term 1 followed by one hundred zeroes.
2. Google started in January, 1996 as a research project at Stanford University by Ph.D students Larry Page and Sergey Brin.
3. 97% of Google revenue comes from their advertising services.
4. The biggest break in search came when Google introduced their improved spell checker seen as 'Did you mean?'. This feature doubled their traffic.
5. The infamous 'I’m feeling lucky' button is nearly never used. However, in trials it was found that removing it would somehow reduce the Google experience. Users wanted it kept. It was a comfort button.
Units of Computer Memory measurements.

If ur pen drives get infected wid the new "SHORTCUT VIRUS" then u can remove it using this simple method.....
1. Open cmd as administrator;
2. type the command
attrib -h -r -s /s /d X:\*.*
(Replace X with ur pen drive letter)
DONE!!
Also, create an 'Autorun.inf' blank file in pen drive & make it read only or inaccessible from security tab which will possibly prevent this infection...
Please correct a common mistake friends 1Kbps is not 1KBps. There's a a small difference of b which makes a huge difference in MBps and Mbps.
None the less many people do confuse in these terms and do get happy when they hear that their internet speed is 1Mbps but actually its 128KBps and complain after wards 'That my speed is 1Mbps but still it doesn't download a 4MB file in 4 secs. :p
Kbps means Kilo'bits' per second not Kilo'bytes' per second.
Since Bytes is a huge amount in relation to networking so most networkoperators give the data transfer in Kilo'bits' not Kilo'bytes' while all the computer files exists in bytes.
To convert bits to bytes divide that databy 8 (since 1byte = 8bits). So next time when you buy a modem or get a connection do check the 'b' and find out its real speed. :D
India's first 1Gbps Internet connection...
Google, launched its 1000mbps (1gbps) at kansas city (US), a leading techn incubator in US, as part of the Google Fiber Network. and Now, it is India's turn to get this speed.
Kerala, India's first telecom company incubator now has a new 1Gbps connectivity, Startup village of Kochi has become the second place in the world, after Kansas city of US.
Start up Village aims to build the elements of a world class tech ecosystem to realize the dream of a Silicon Coast in INDIA.
you can download a two-hour HD movie in 30 seconds or view 1080p video in YouTube at this lightning speed ....
#addy#

Which one would u like to buy..????
All features of top smartphones are listed here...
Open Cmd and Type
-debug
Enter then type
- DF000:FFF5
Hit Enter...
DID YOU KNOW??
Facebook paid a whooping $8.5 Million to buy "Fb.com" domain!! So next time instead of typing "facebook.com" you can just type in "Fb.com" to save time!!
Languages Used....
1. Google – Java (Web), – C++ (indexing)
2. Facebook – PHP
3. YouTube- Flash, Python, Java
4. Yahoo– PHP and Java
5. Microsoft Live.com– .NET
6. Baidu – Unknown
7. Wikipedia – PHP
8. Blogger – Java
9. MSN – .NET
10.Twitter – Ruby on Rails, Scala, Java
1. Those who use trial versions of softs..
2. Go to GOOGLE.com
3. Type '94fbr' Then space and then name of software u need..
4. Google will show u links with ur desired serial key or patch files..
SOME INTERESTING FACTS ABOUT GOOGLE:
1. The name GOOGLE was an accident. A spelling mistake made by the original founders who thought they were going for GOOGOL. Googol is a mathematical term 1 followed by one hundred zeroes.
2. Google started in January, 1996 as a research project at Stanford University by Ph.D students Larry Page and Sergey Brin.
3. 97% of Google revenue comes from their advertising services.
4. The biggest break in search came when Google introduced their improved spell checker seen as 'Did you mean?'. This feature doubled their traffic.
5. The infamous 'I’m feeling lucky' button is nearly never used. However, in trials it was found that removing it would somehow reduce the Google experience. Users wanted it kept. It was a comfort button.
Units of Computer Memory measurements.

1. Open cmd as administrator;
2. type the command
attrib -h -r -s /s /d X:\*.*
(Replace X with ur pen drive letter)
DONE!!
Also, create an 'Autorun.inf' blank file in pen drive & make it read only or inaccessible from security tab which will possibly prevent this infection...
Please correct a common mistake friends 1Kbps is not 1KBps. There's a a small difference of b which makes a huge difference in MBps and Mbps.
None the less many people do confuse in these terms and do get happy when they hear that their internet speed is 1Mbps but actually its 128KBps and complain after wards 'That my speed is 1Mbps but still it doesn't download a 4MB file in 4 secs. :p
Kbps means Kilo'bits' per second not Kilo'bytes' per second.
Since Bytes is a huge amount in relation to networking so most networkoperators give the data transfer in Kilo'bits' not Kilo'bytes' while all the computer files exists in bytes.
To convert bits to bytes divide that databy 8 (since 1byte = 8bits). So next time when you buy a modem or get a connection do check the 'b' and find out its real speed. :D
03/05/2013
Trick on How to check your pen drive original or fake?
Trick on How to check your pen drive original or fake?
Nowadays we can buy Flash drive at low price. We can buy 32GB flash drive for only 10 $. Mostly these are fake drives. Now flash drives also manufactured as fake and its it’s look like original one. These type flash drives are mostly imported from China. They are using some small programs to show 4GB pen drive as 32GB.

1. H2Testw software is one of the best software to check Pen-drive is original or not. Also you can check your Memory Card with this software.
Click here to Download H2Testw. (mediafire) or Download this software here.(ziddu)
2. Unzip/Extract the file and run the application file.
3. Before checking a pen drive, empty the files and folders.
4. Click Target device and select your removable device.
5. Click Write+Verify button and wait for your pen drive being checked.
6. If your pen drive is verified as original one, it will be displayed as “Test finished without errors”
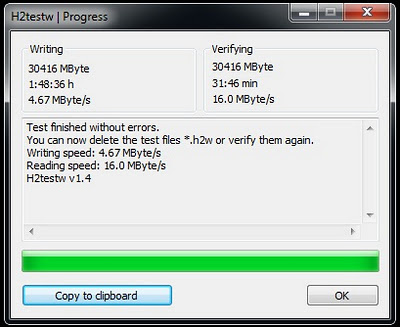
7. If your pen drive is fake one, it will be displayed as “The media is likely to be defective”
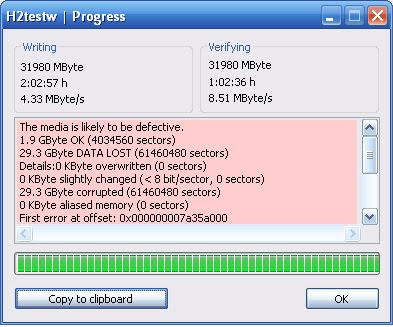
This software displays read/write speed and errors of your usb drive. If your usb device is damaged, you will see some errors. you can select also internal hard disk drives for this verifying method.
Changing your video files to audio files easily
Changing your video files to audio files easily
-----------------------------------------------------------
Have you ever thought of changing your video files easily without much trouble ? Then here is the trick… We are going to use Vlc player to change the files. Download Vlc- http://majorgeeks.com/VLC_media_player_d4674.html
We have provided a picture so it can be easy to understand. It will not be in order with the steps given below. It will be given in short and easily viewable screen shots which are numbered in its own order. SO DON’T CONFUSE IT…
1)Open Vlc and press Ctrl + R.
2)Now a window like the one shown in the picture below will be opened.
3)Now press add and add your video file.
4)Press Convert/save button on the bottom of the window.
5)Now select a destination for your file. Ex: you want it to be in Desktop after it is changed then select desktop.
6)Now type a name for it and add .mp3 or .mp4 to the name. Example: Suvavemente-Pitbull.mp3
7) Now if you are done. Select the type you want to change it to. As we are converting it to an audio file here , you can choose Audio-Vorbis,Audio-Mp3 or Audio-Mp3(Mp4)
8)The select start and wait for about 5 minutes(my estimated time) . (It took me 3-4 minutes to change a 3 minute song to audio. Maybe it was done before that but I checked it only after 4 mins) ;)
9)Don’t wait all day long. Just check it out by pausing the vlc which now will be buffering. If the song is all loaded and finished it will be like show in the pic. So close Vlc and check out the new video file.
Note: I tried only short video files, the longest I tried was 7 mins .. You can try your own, but I am not giving you any guarantee that it will work with long videos. But I think it will :)
So,All is well. If you have any trouble just check out the pic.Enjoy!!!
-Ciao.

Collected from - Tricks World..
Technical Interview Demystified
Technical Interview Demystified
Technical Interview
In this section i will tell you how easy it is for a fresher to clear a technical interview stated if he follows the basic tips/rules/mantra:
Technical Interview is part of the recruitment process for almost all the companies and this is the second biggest elimination round after the written test.
Well, I will assume here as you are a fresher trying to get into a software company (since most does irrespective of their branch).
Any software firm small or big wants their employees to know the basics of the subjects like,
Programming
software engineering
operating systems
Databases
Computer Networks.
Having said that they won’t expect you to know every part and parcel of the subjects, rather they would look for someone who at least knows what they are for.
Now if you are asked to write a C-Program which does check whether a given integer/string is a palindrome or not (which is part of lab programs for almost all the universities in the country in the 1st year), he would expect that you will write it easily and if you fail to do so, please don’t expect him to select you.
So what would we suggest is that, you should have basic knowledge on the aforementioned subjects and we will also tell you the areas you should concentrate in each subject.
1. Programming
In any technical interview, it is obvious that you would be asked to write some programs and mostly in C,C++ & Java .
To be confident at this area, you should know the basic syntax of all these subjects as the semantic or logic remains the same.
Start with C, learn variables, operators, control structures, functions & pointers (the most important stuff), structures and files. Then go for C++ and java, try to understand the differences between all the three precisely.
OOPS is the most important & probable topic, where you might get questions from.
Below is the list of the most frequently asked programs that you must learn to clear this round.
a) Write a C program to swap two numbers without using a third variable.
b) Write a C program to check whether the given number or a string is palindrome or not.
c) Write a C program to create a Pascal triangle.
d) Write a C program to perform matrix multiplication and addition.
e) Write a C program which performs bit manipulation (&,|,etc) of a given number.
f) Also, learn programs which does basic file manipulations (creation, writing data and reading)
2. Software Engineering
This is the most important & also a boring subject, since it is mostly theoretical.
Not many interviewers ask questions on this subject in the technical interview, but it is always better to know the basics and be on the safer side.
Questions in this subject would be basically on the following topics,
a. Phases of Software Development Life Cycle
b. Process Models like Waterfall model, agile model etc.
c. Cyclomatic complexity of a software
d. Basics of software testing(white box, black box testing)
If you can learn all these, then you could possibly answer all the questions in the interview.
3. Operating Systems
Define operating system?
Could be the first possible question in some technical interview’s and this subject is one of the core subjects of computer science. Students from CS and IT back ground can’t take any excuses for not answering questions in this subject and others may get excuse if you don’t answer.
Now in this subject, you have to know the following things:
a. The definition of an Operating System, components of an OS(like process management, memory management , etc)
b. Learn the functionality of all the cpu scheduling algorithms like FCFS,SJF, Round-Robbin , etc.
c. Learn how process synchronization works, this concept involves semaphore, monitor to achieve process s synchronization.
d. Learn basic memory management techniques like paging, segmentation etc.
This should do for answering any question in Operating System.
4. Databases
No application works without a database and so it is must for us to know the basics of the data base management system.
Do learn the following things,
a. Whenever we say DBMS we refer to RDBMS and everything is relational here in this DB. Go through the basics like entities, attributes and relations,ER-models,keys and constraints.
b. Now learn to implement them with the structured query language shortly called as SQL, learn the basic operations CRUD(create, insert ,update & delete).
These all should do,but also go through transactions which is also an important concept and might be asked in the interview.
5 .Computer Networks
Stand alone systems don’t do any wonders and that is why the systems are connected through a network.
In computer networks all you need to concentrate is on the OSI reference model which covers everything, do try to know what each layer does and know about TCP,IP in particular.
This should do for computer networks.....
Projects/Internships & Papers Presented (Optional)
Project is part and parcel of the curriculum for each and every engineering student and the quality of this project shows the student’s experience, expertise and exposure to various technologies and methodologies.
Now when you were asked this question,
Tell me about your projects (or) what are all the projects you have done?
Many wonder where to start, so let me clear your doubts about this here. Now before you answer this question, you should know the following basic things about your project:
Your Project Name (don’t laugh this happened before and I saw people not able to pronounce their project names)
Reason for choosing this project over many other projects present out there, I mean the idea behind this project.
Technologies used and your role in the project.
Entire project architecture and design (includes UML diagrams and Schema)
You should be able to write part of the code from your project (not certain that you will be asked about this).
Problems faced during the project (if you have done your project, else use the famous words like “faced problem with requirement gathering”, “problem with some part of code which you were not able to do”) and you should also explain about how you have overcome them.
When the interviewer asks about projects , he /she knows that only 1% of the whole engineering students genuinely do the projects as many would only pay money and get the source code, having said that they would only expect you to know the basics of what every project in common has.
So, please make sure that you know the architecture/design of the project and practice well about how to demonstrate your project in an efficient way.
Papers
Not everyone would have presented papers in conferences and symposiums, but if you have done so and kept them on your resume be ready to answer some simple questions on the topics you have presented.
You may be asked to give a shorter version of that presentation which you given previously or you might be asked to assume that there is a slide show of your presentation and give a mock demo(who knows, you might be asked)
Well I have tried my level best to give you the idea about the questions asked in technical interviews in the best possible scenarios...
Finally, I would say this :
“In this world of uncertainty, nothing is certain and so every interview is unique in its own way and to be through the interview, prepare well for the worst possible scenario and give your best and success would follow”
If there is anything you would want to ask, please add a comment and I would respond or mail us...
Keep Visiting for more technical stuffs....!!
Do share if you like this...
Do share if you like this...
Leave ur valuable feedback...
Beware of Internet virus that steals bank a/c details, password
Beware of Internet virus that steals bank a/c details, password
The malware steals credentials like file transfer protocol passwords, bank account logins, infects removable media and changes browser settings
A new virus has been found to be “spreading widely” in the Indian cyberspace which cleverly steals bank account details and passwords of the user once it is clicked.
Country’s cyber security sleuths have alerted Internet users in the country about the new and suspected variant of malware family called ‘Win32/Ramnit’.
The malware, the advisory states, “steals credentials like file transfer protocol passwords, bank account logins, infects removable media, changes browser settings and downloads and executes arbitrary files”.
The virus is so deadly and potent, cyber sleuths say, that it has ability to hide itself from anti-virus solutions and acquires various aliases to attack a genuine system or Internet-based connection which works to play emails and other user services.
The virus is such lethal in its operations that it “infects the removable media by copying itself to its recycle bin and creates an autorun.Inf file,” the advisory said.
Once the system is infected, the malware injects its code into windows executables, html files or dlls to communicate with its command and control server, thereby compromising the security of the online system.
The agency has also advised some counter measures in this regard.
The combat steps against this virus stipulate that users should not download and open attachments in emails received from untrusted users or unexpectedly received from trusted users, one should exercise caution while visiting links to web pages and users should not visit untrusted websites.
“Enable firewall at desktop and gateway level and disable ports that are not required, avoid downloading pirated software, keep up-to-date patches and fixes on the operating system and application softwares and keep up-to-date anti- virus and anti-spyware signatures at desktop and gateway level,” the advisory stated.
Source : Business Standard
02/05/2013
People Who Changed the Internet Forever..!!
Top 25 People Who Changed the Internet Forever ---
1. Sir Tim Berners-Lee – World Wide Web
2. Vint Cerf And Bob Kahn – TCP/IP
3. Larry Page and Sergey Brin – Google Inc.
4. David Filo and Jerry Yang – Yahoo! Inc.
5. Bill Gates – Microsoft
6. Steven Paul Jobs – Apple Inc.
7. Mark Zuckerberg – Facebook
8. Chad Hurley and Steve Chen – YouTube
9. Linus Torvalds – Linux
10. Jack Dorsey – Twitter
11. Kevin Rose – Digg
12. Bram Cohen – BitTorrent
13. Mike Morhaime – Blizzard Entertainment
14. Jimmy Wales – Wikipedia
15. Jeff Preston Bezos – Amazon
16. Shawn Fanning – Napster, Rupture
17. Pierre Omidyar – eBay
18. Jack Ma – Alibaba
19. Craig Newmark – Craigslist
20. Matt Mullenweg – WordPress
21. Thomas Anderson – MySpace
22. Garrett Camp – StumbleUpon
23. Jon Postel – Internet Pioneer
24. Caterina Fake – Flickr
25. Marc Andreessen – Netscape
Thanks 2 all these great persons,bcoz of them v are getting a lot of benefits from web....!!!!!!!!
1. Sir Tim Berners-Lee – World Wide Web
2. Vint Cerf And Bob Kahn – TCP/IP
3. Larry Page and Sergey Brin – Google Inc.
4. David Filo and Jerry Yang – Yahoo! Inc.
5. Bill Gates – Microsoft
6. Steven Paul Jobs – Apple Inc.
7. Mark Zuckerberg – Facebook
8. Chad Hurley and Steve Chen – YouTube
9. Linus Torvalds – Linux
10. Jack Dorsey – Twitter
11. Kevin Rose – Digg
12. Bram Cohen – BitTorrent
13. Mike Morhaime – Blizzard Entertainment
14. Jimmy Wales – Wikipedia
15. Jeff Preston Bezos – Amazon
16. Shawn Fanning – Napster, Rupture
17. Pierre Omidyar – eBay
18. Jack Ma – Alibaba
19. Craig Newmark – Craigslist
20. Matt Mullenweg – WordPress
21. Thomas Anderson – MySpace
22. Garrett Camp – StumbleUpon
23. Jon Postel – Internet Pioneer
24. Caterina Fake – Flickr
25. Marc Andreessen – Netscape
Thanks 2 all these great persons,bcoz of them v are getting a lot of benefits from web....!!!!!!!!
Subscribe to:
Comments (Atom)


